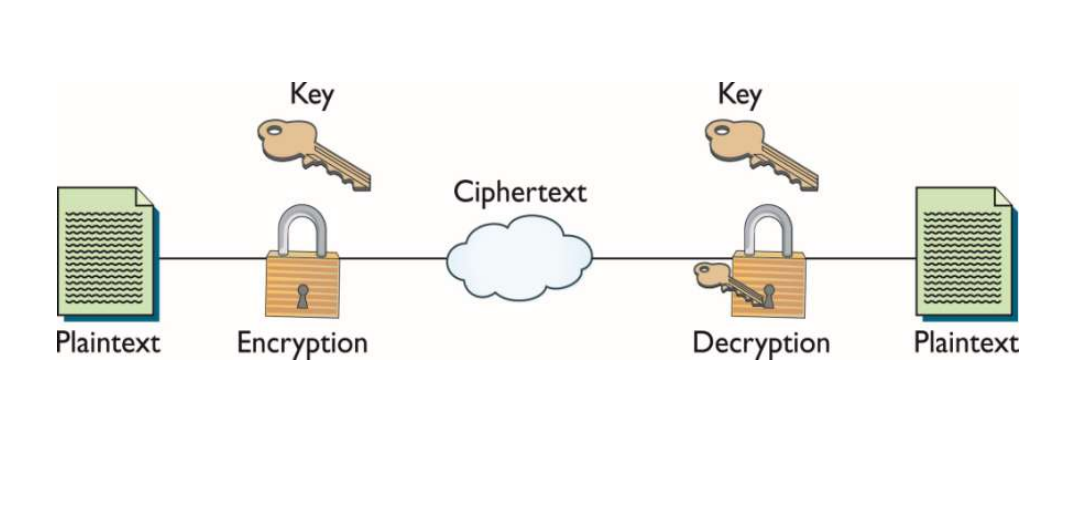
What is cryptography? Symmetric key cryptography flowchart What is cryptography? data flow diagram of cryptography
Algorithm Analyzing Digital Cryptography Data Flow Stock Vector
Data flow encryption/decryption process Cryptography introduction cryptanalysis cryptographic decryption algorithms Cryptosystem cryptography transfer data cryptosystems illustration sender wants shows who some scanftree compromised
Cryptography types diagram block source
Data encryption processing flowCryptography symmetric key diagram using techniques involves exchange steps message following The flow chart of the data encryption programData flow diagram for the cryptosystems.
Data cryptography processFlow chart diagram for the encryption and decryption process Cryptography diagramData flow diagram (encryption).

Cryptography key symmetric cryptographic algorithms system edureka types encryption transposition securing implemented information ciphers works introduction
Data flow diagramThe flow chart diagram for the encryption and decryption process (a) correct result of decryption. (b) save image to file.The cutting edge for your business- ecommerce.
Crypto diagram blockchain flow system database algorithm hash based decentralized ledger technologyData processing flow in an encryption Encryption isometric flowchartFlowchart for encryption and decryption download scientific diagram.

Basic flow chart of data encryption and decryption.
Encryption decryption processAlgorithm analyzing digital cryptography data flow stock vector Cryptosystem cryptography cryptosystems model basic illustration tutorialspoint simple information confidentiality discuss depicted transmitted belowTypes of cryptography.
Flowchart cryptography symmetricCryptography used cryptographic techniques definition ciphers blockchain algorithms protecting cissp method Cryptography securing implemented chfData encryption flow chart for the proposed algorithm.

A comprehensive guide to the data encryption standard (des) algorithm
In process flow diagram data items blue prismSymmetric key cryptography Flowchart showing the encryption and decryption modules of the systemDecryption process flow diagram..
Flow diagram of encryption.Uml for explaining cryptography. uml diagrams can be used to explain Data encryption isometric flowchart stock vectorData flow diagram showing how data from various sources flows through.

Cryptographic communication process data flow chart
.
.